Why is it necessary to scan for vulnerabilities on WordPress using VirtualBox? As the popularity of the WordPress content management system grows, so do the associated security risks. To protect confidential information from hackers and cyber attackers, it is necessary to scan and identify vulnerabilities within WordPress enhancing the site’s security. In this tutorial, we will explore how to scan for vulnerabilities in WordPress using VirtualBox.

Why you should be using VirtualBox?
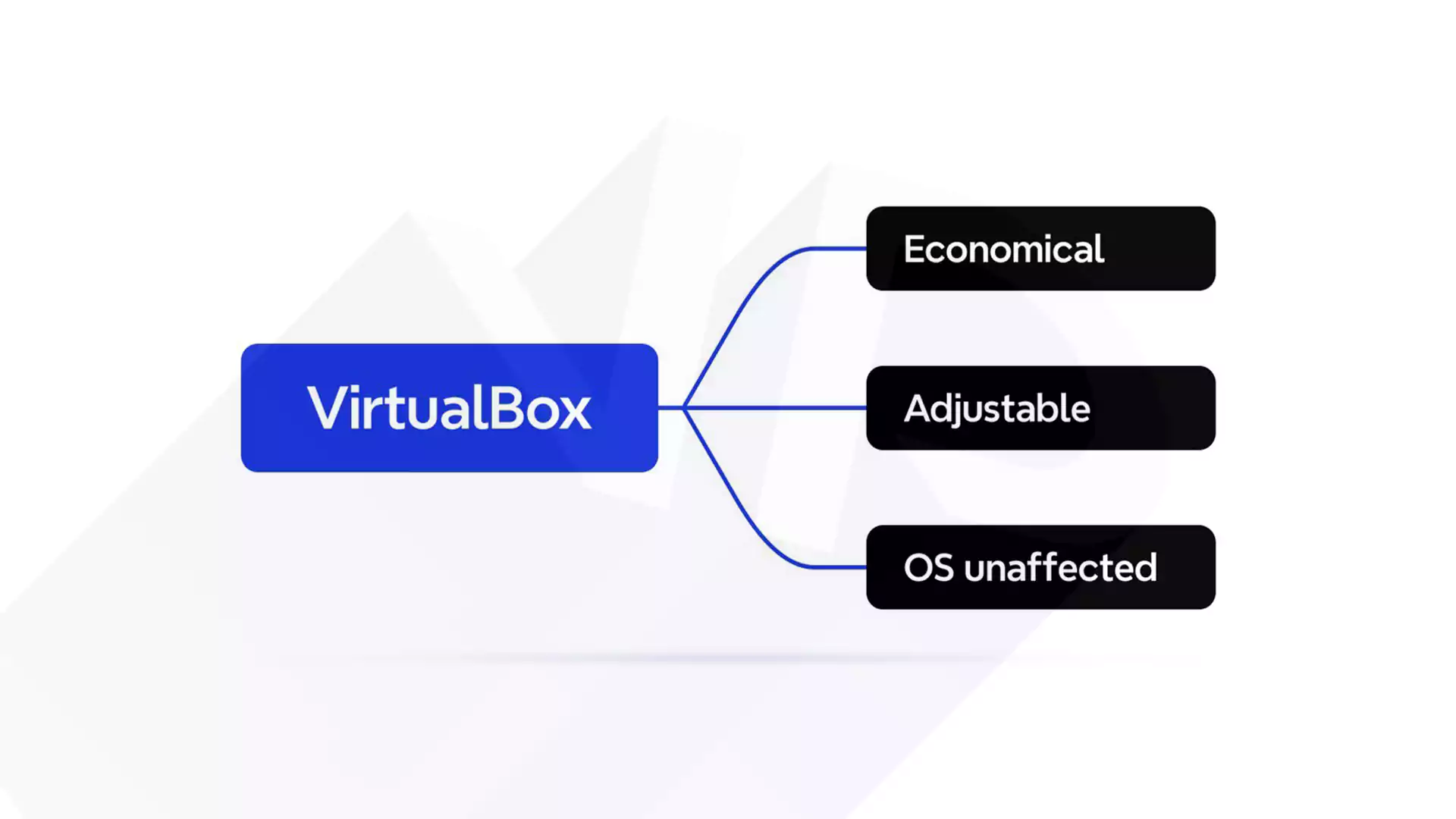
VirtualBox is a suitable option for scanning your WordPress site for vulnerabilities for the following reasons:
- Your OS remains unaffected
By using VirtualBox, your operating system will be fine. - Economical
VirtualBox has an accurate scanning capability and is free to download. - Customizable
Configure your virtual machine using VirtualBox to run a security test indirectly on a live site.
Top way to scan vulnerabilities on WordPress using VirtualBox
For scanning weaknesses of your WordPress site by using VirtualBox, complete these setup instructions:
1- Download and Setup VirtualBox
First, select the latest version that your operating system is compatible with and download it.
To learn how to scan these weaknesses, you’ll need a Linux-based operating system that is as secure as possible with security tools.
One of the most important steps in scanning is correctly configuring the Bridget Adapter network settings to directly connect your virtual environment to the network. Adjusting these settings will enable your virtual machine to access your WordPress site.
2- Setting up WordPress in VirtualBox
Now it’s time to install WordPress. First, we need to set up and configure A LAMP stack to run WordPress in the Ubuntu virtual environment.
sudo apt update sudo apt install apache2 mysql-server php libapache2-mod-php php-mysql
Now, download and setup WordPress:
cd /var/www/html sudo wget https://wordpress.org/latest.tar.gz sudo tar -xvzf latest.tar.gz sudo chown -R www-data:www-data /var/www/html/wordpress
To configure WordPress,Please set up a MySQL database in the following file:
wp-config.php
3- Tools for ScanWordPress vulnerabilities using VirtualBox
Next, we would like to introduce 3 powerful tools with the help of which you can easily scan WordPress vulnerabilities using VirtualBox:
This tool checks and finds vulnerabilities such as old plugins, unsecured passwords, and security problems. 
For setting up WPScan:
sudo apt update sudo apt install wpscan
To use WPScan:
wpscan --url http://your_ip_address/wordpress
- Nikto
Nikto is one of the best tools to scan your WordPress site’s vulnerabilities using VirtualBox. It identifies server setup errors and antiquated parts.
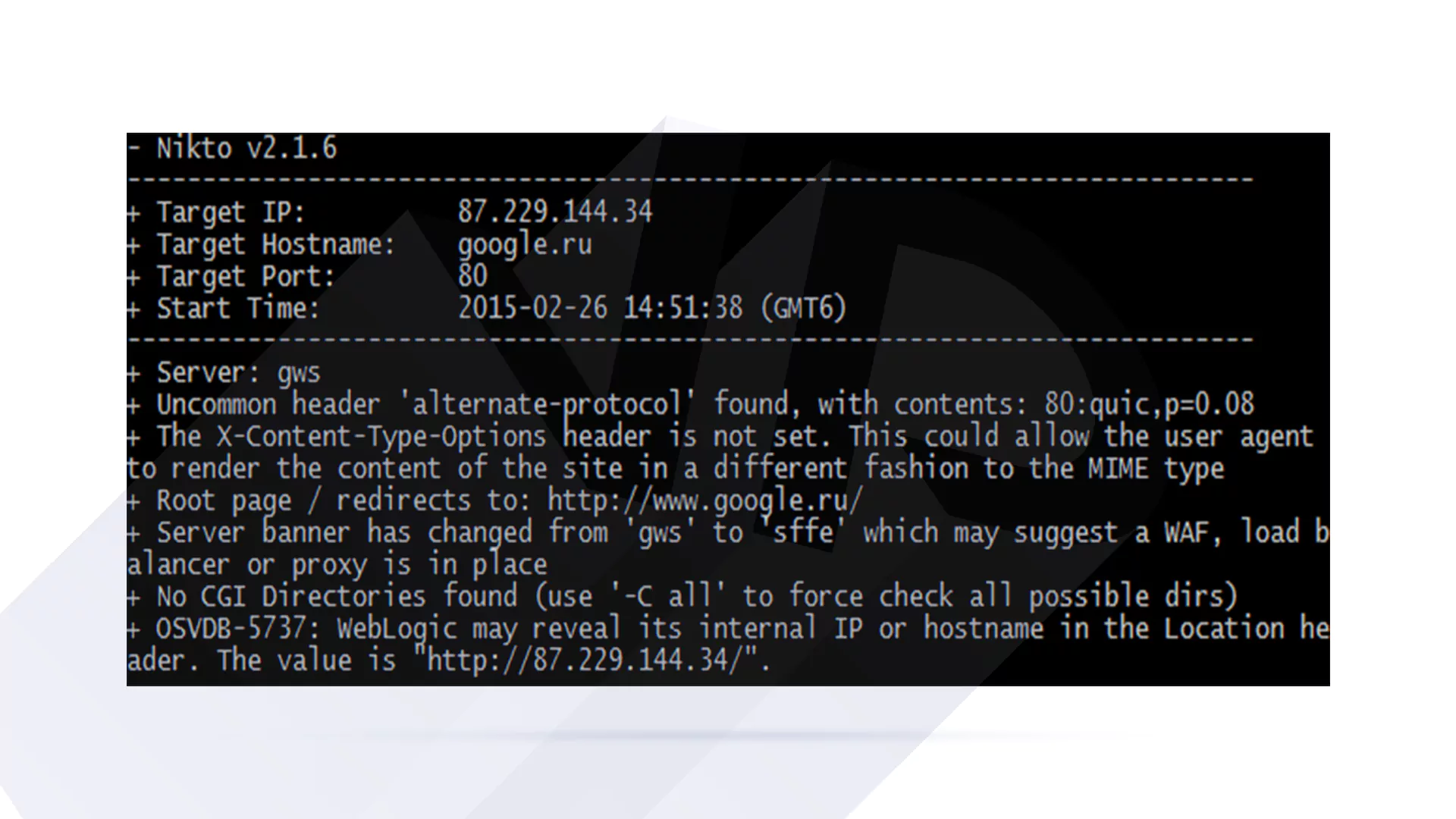
For setting up Nikto:
sudo apt install nikto
To use Nikto:
nikto -h http://your_ip_address/wordpress
Burp site identifies and monitors user traffic and interactions besides scanning injection areas and cross-site scripting issues.
After downloading and running Burp Suite, you must configure your browser to redirect traffic through this site.
4- Managing vulnerabilities
It’s good to know that simply identifying vulnerabilities is not enough., and the measures and solutions provided below must be used to fix or reduce these vulnerabilities so that the results obtained will improve the security of the site.
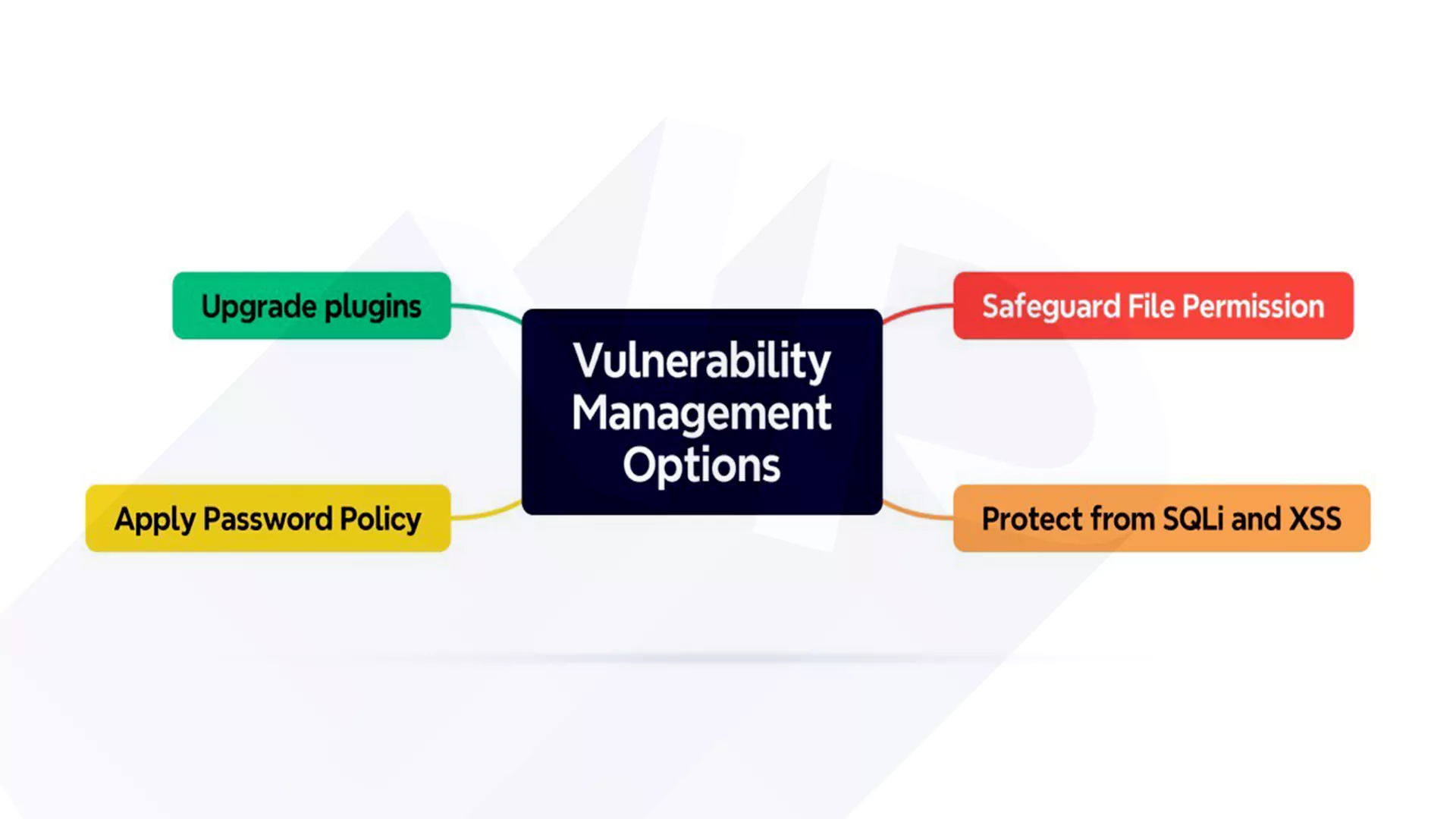
- Upgrade plugins
- Apply Password Policy
- Safeguard File Permission
- Guard Against SQL injection and cross-site scripting
5- Establishing Security Enhancements on the Live Site
The following tips are for better implementation of improvements on the live site, after scanning vulnerabilities on WordPress using VirtualBox :
- Update WordPress core and plugins. and themes
- Install a WordPress security plugin such as Wordfence
- Setup alerts for suspicious login attempts
- Create a backup plan for data recovery
Conclusion
Regular vulnerability scans and proper security utilization will help keep WordPress websites secure and protect user information. You don’t have to worry about troubleshooting a WordPress site because your scans are isolated when scanning in VirtualBox. By using the methods discussed in this tutorial, you can help improve the security of websites and prevent potential risks.
